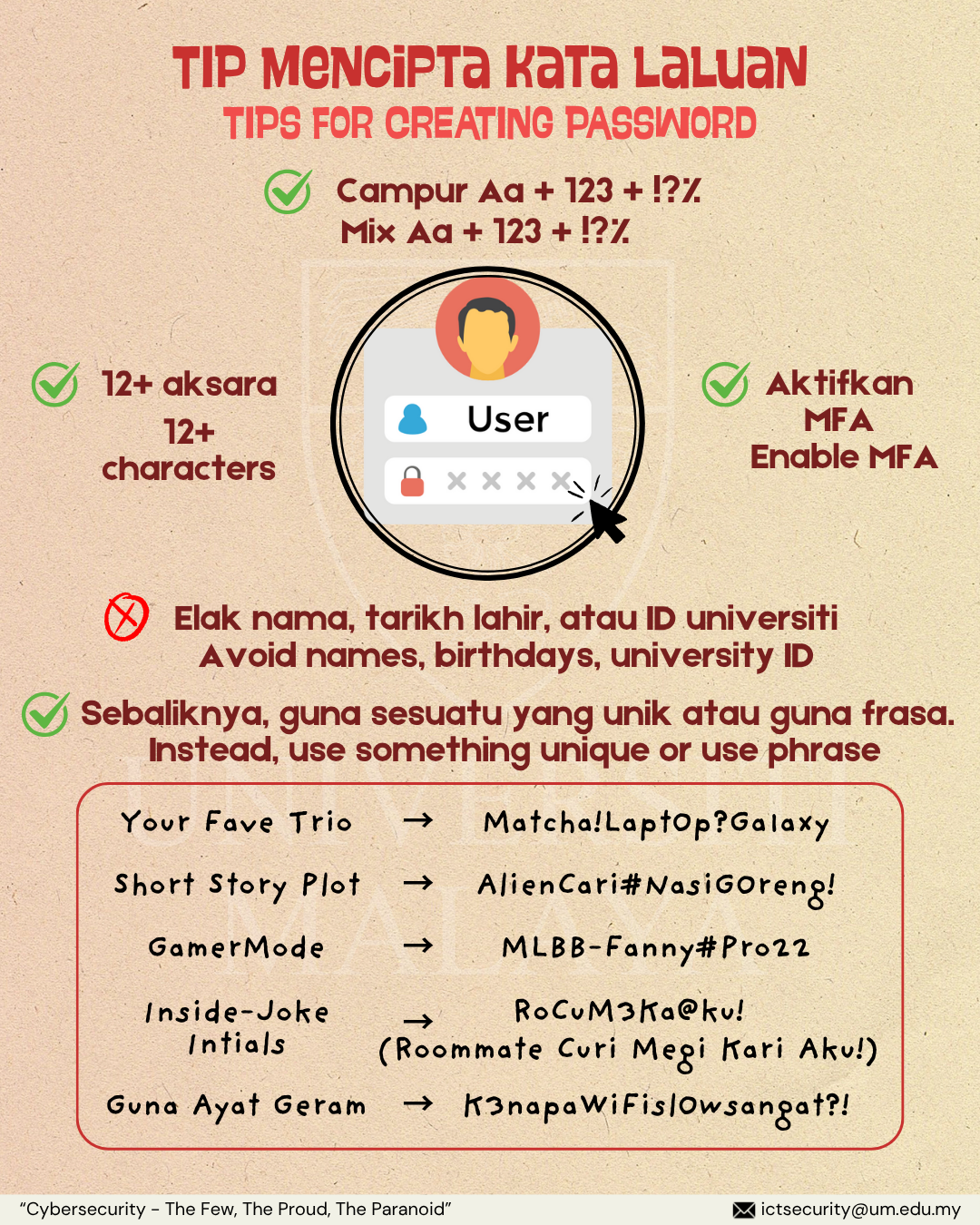
Never Give Out Your Password
- Guard your password just as you guard your bank card PIN.
- Never write your password down.
- Never share your password with anyone.
- Never say “yes” when your browser asks you if you’d like to save your password.
- Never send your password in email, even if the request looks official.
- Update your password frequently.
Link to update your UMMail password.
Beware of fake anti-virus software scams
- Keep your computer updated with the latest anti-virus and anti-spyware software, and be sure to use a good firewall.
- You need at least 3 components to ensure proper PC security.
- Get anti-virus software from PTM(Only for UM computers - UM staff)– To make a request, go to UM Helpdesk. Click HERE
- Never open an email attachment unless you are POSITIVE about the source.
- Do NOT download freeware or shareware unless you know it's from a reputable source
Social Engineering via Social Networking
Be careful when using Social Networking Websites such as Tiktok, Instagram, Facebook, X & Threads.

Monitor your Email Last Account Activity
If you suspect your UMMail/Siswa Mail account has been hacked or just want to make sure it hasn’t, please regularly check your UMMail Last Account Activity record.

Back Up Your Files

Do-iT- Yourself : Security Updates
Keeping your operating system up to date is critical. Running whatever antivirus you have in your computer is NOT enough. You can configure your computer to automatically seek out updates.
Phishing Tips

Manage your exposure to Malware/virus
- Malware, or malicious software, is hostile, intrusive, or annoying code that includes viruses, spyware, adware, worms, trojan, horses, and other unwanted programs.
- Malware spreads rapidly and by many different ways: for example,e-mail attachments;infected document files; Web sites that contain hostile code that can infect your computer through vulnerable browsers; and unprotected file shares.
- To get the most benefit from your antivirus software ensures it is updated regularly and is operating as intended.
- Be cautious about peer-to-peer sharing networks

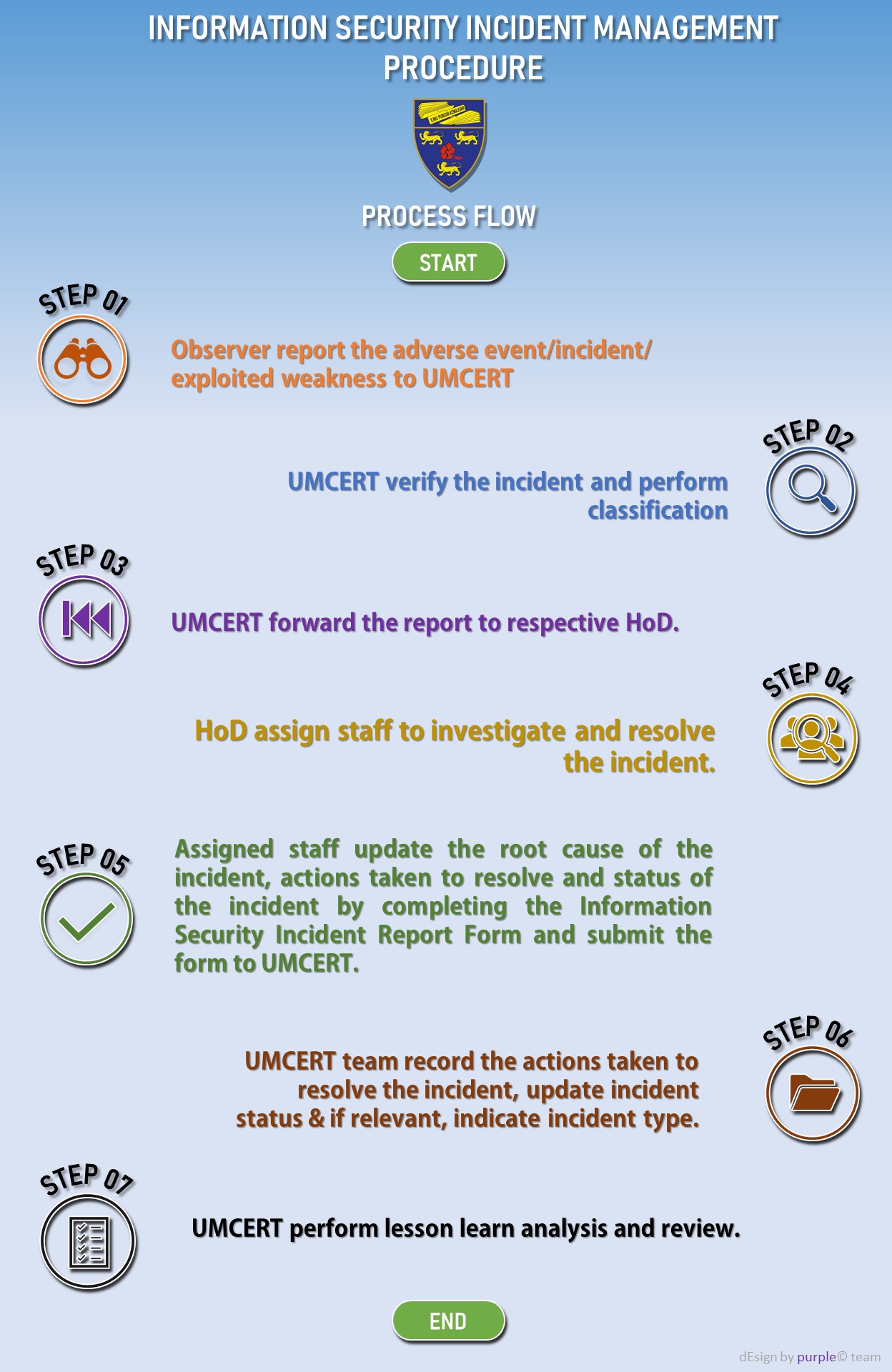
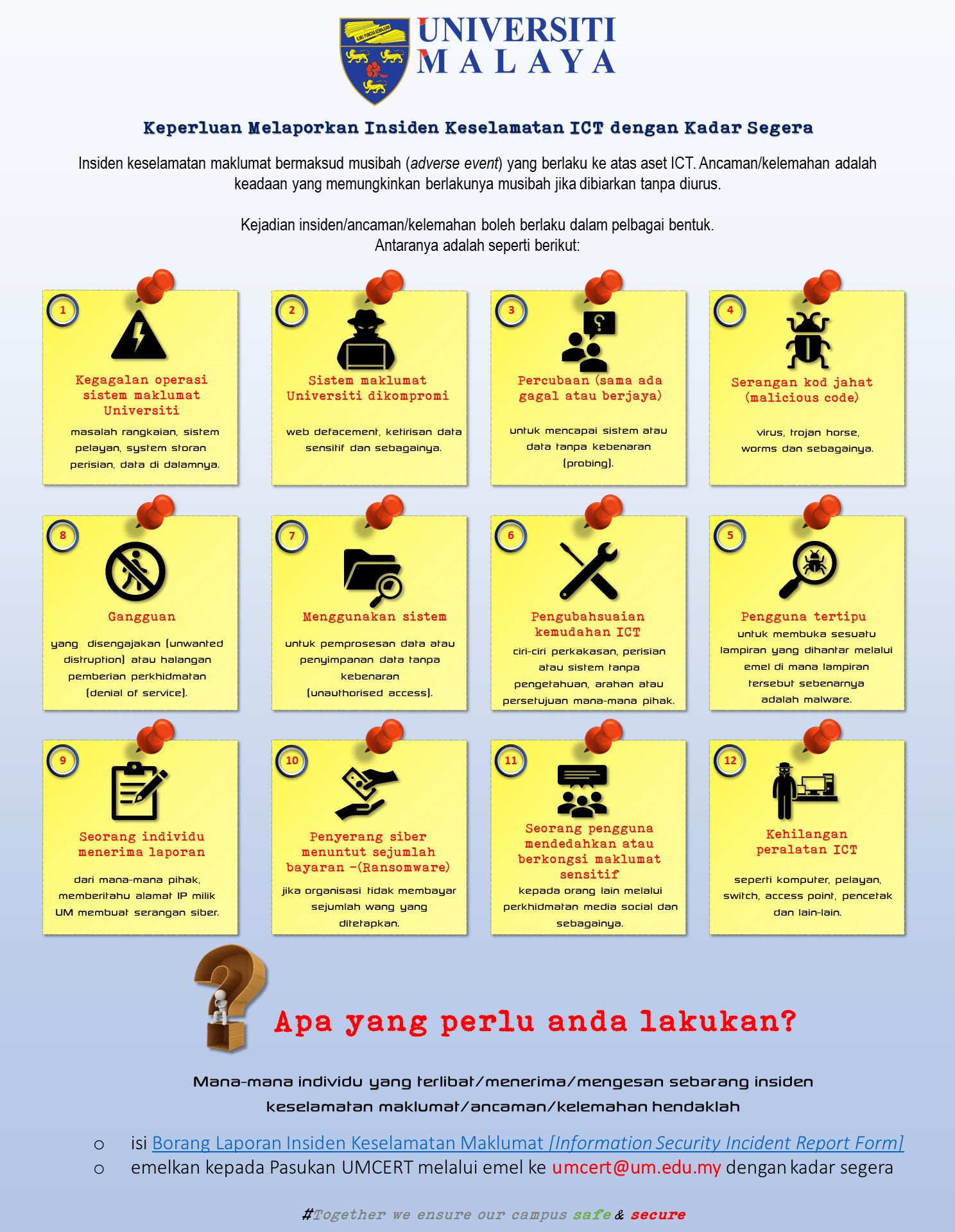
ICT Security Incident Reporting Requirements
Information Security Incident Management Procedure
Versi Bahasa Malaysia

Untuk keterangan lanjut,sila klik PROSEDUR PENGURUSAN INSIDEN KESELAMATAN MAKLUMAT
How to keep your workplace SECURE?
Together we ensure our campus safe & secure
Versi Bahasa Malaysia

Untuk lebih terperinci, sila klik :- PERATURAN DAN KAEDAH PENGGUNAAN KEMUDAHAN ICT